EDL tools and Cross-platform EDL mode usage (Qualcomm devices)
EDL is an interface of Qualcomm chipsets, used to flash fastboot ROMs. It is used for unbricking purposes so it is allowed on many phones but it's been locked down on most recent Android models.
The screen will appear black and it will appear that the device is turned off, but to verify that this is not the case, we need the tools in EDL mode. The most famous is QFIL (Qualcomm Flash Image Loader), a proprietary software, but on GitHub there are many alternative open source projects.
Since we have a lot of Qualcomm-based devices, some of them can be quirky to guess how to enter EDL mode, or how to do it correctly, for instance:
On Alcatel Cingular Flip you have to first hold both volume keys, then only one of them;
On CAT B35 you have to hold * and #;
On Nokia 8110 4G you have to hold Up and Down, and during this you must insert the cable.
It is important to know first how to access EDL mode on the KaiOS device. You can try a variety of combinations like the ones just described.
Open source tools successfully tested...
Here is a list of EDL tools successfully tested on each KaiOS phone:
Click the link to the repositories, it will open a GitHub page with all the instructions on installing the tool and the commands to be used;
Click on the device icon to enter the page of the "KaiOS DEVICES" section where you can download the dedicated firehose loader.
...on Alcatel OT-4044O and CAT B35
All tests were carried out by Luxferre.
...on Nokia 8110 4G and Alcatel OT-4044x
The tests on Nokia 8110 4G were carried out by Scottz.
...on Alcatel A405DL MyFlip
All tests were carried out by LiKiWii U (on Discord) and Yossi.
Example of cross-platform EDL mode usage
Here is the basic guide of how to use EDL mode of Qualcomm-based devices specific for the plugnburn (by Luxferre, forked from B. Kerler) and andybalholm tools, without any proprietary dependency.
Prerequisites
Python 3.7 64-Bit;
Firehose loader binaries for your device (for example, on edl.bananahackers.net and Google Groups)
Installation
Clone the repository and install the dependencies:
git clone https://github.com/plugnburn/edl
sudo -H pip3 install pyusb pyserial capstone keystone-engine
if you're running Linux and having issues with device access, append "blacklist qcserial" to "/etc/modprobe.d/blacklist.conf", copy 51-edl.rules to /etc/udev/rules.d and 50-android.rules to /etc/udev/rules.d
NOTE, in all the next examples we will use a firehose for CAT B35, "generic_CAT_B35.mbn", you have to enter the exact name of your firehose.
Get the partition layout
using the command "python3 edl.py -loader generic_CAT_B35.mbn -printgpt", you should get something like this:
GPT Table:-------------modem: Offset 0x0000000004000000, Length 0x0000000004000000, Flags 0x00000010, UUID 57ffe7f2-aa66-6de8-4925-6e456356ed0f, Type EFI_BASIC_DATAsbl1: Offset 0x0000000008000000, Length 0x0000000000080000, Flags 0x00000000, UUID f4d0d804-0d40-b192-52e1-037b21fc5d34, Type 0xdea0ba2csbl1bak: Offset 0x0000000008080000, Length 0x0000000000080000, Flags 0x00000000, UUID fa17d830-faac-f42e-1ca6-e5f3909ed83d, Type 0xdea0ba2caboot: Offset 0x0000000008100000, Length 0x0000000000100000, Flags 0x00000000, UUID 72348d8d-8980-e1e0-2147-cd4bfb15cc76, Type 0x400ffdcdabootbak: Offset 0x0000000008200000, Length 0x0000000000100000, Flags 0x00000000, UUID 15ae6f30-62fe-535d-26e8-7b45ec3f2f61, Type 0x400ffdcdrpm: Offset 0x0000000008300000, Length 0x0000000000080000, Flags 0x00000000, UUID 621608ec-4c27-408b-88f6-f7112f08bff2, Type 0x98df793rpmbak: Offset 0x0000000008380000, Length 0x0000000000080000, Flags 0x00000000, UUID 7d8b0a0a-a13c-aaac-0c2f-af22770dd414, Type 0x98df793tz: Offset 0x0000000008400000, Length 0x00000000000c0000, Flags 0x00000000, UUID 006b839f-92b4-e8ea-eed6-4e322c99fa16, Type 0xa053aa7ftzbak: Offset 0x00000000084c0000, Length 0x00000000000c0000, Flags 0x00000000, UUID 11a435f8-89be-672c-6045-df71b4271292, Type 0xa053aa7fpad: Offset 0x0000000008580000, Length 0x0000000000100000, Flags 0x00000000, UUID 5225287f-492b-eda3-7027-a441b7ea6379, Type EFI_BASIC_DATAmodemst1: Offset 0x0000000008680000, Length 0x0000000000180000, Flags 0x00000000, UUID 6d11e78e-bd73-b78b-339d-0f882b09157b, Type 0xebbeadafmodemst2: Offset 0x0000000008800000, Length 0x0000000000180000, Flags 0x00000000, UUID 617e5535-6e7c-2a68-90ed-774949fd395e, Type 0xa288b1fmisc: Offset 0x0000000008980000, Length 0x0000000000100000, Flags 0x00000000, UUID d0b3277d-6bec-27fd-5a02-4c8eff5abc7a, Type 0x82acc91ffsc: Offset 0x0000000008a80000, Length 0x0000000000000400, Flags 0x00000000, UUID 95419db9-c3cc-9d51-7dca-e7fddb0cea10, Type 0x57b90a16ssd: Offset 0x0000000008a80400, Length 0x0000000000002000, Flags 0x00000000, UUID cfa7e216-23da-8e3b-9165-b730314789ca, Type 0x2c86e742splash: Offset 0x0000000008a82400, Length 0x0000000000a00000, Flags 0x00000000, UUID f59b020c-7407-578b-d8f4-7608c01dbbe1, Type 0x20117f86DDR: Offset 0x000000000c000000, Length 0x0000000000008000, Flags 0x00000010, UUID bbf8967c-4e6b-aaee-8a1d-d1536fd84c2d, Type 0x20a0c19cfsg: Offset 0x000000000c008000, Length 0x0000000000180000, Flags 0x00000010, UUID 0fe0230c-96c2-7c89-8325-16343e46d20f, Type 0x638ff8e2sec: Offset 0x000000000c188000, Length 0x0000000000004000, Flags 0x00000010, UUID 52a9a7ef-d31f-045a-cb5a-0da0a0ea29b1, Type 0x303e6ac3boot: Offset 0x000000000c18c000, Length 0x0000000002000000, Flags 0x00000010, UUID 76b6ddd6-e0fd-b9b9-904b-9755e3004bcd, Type 0x20117f86system: Offset 0x000000000e18c000, Length 0x0000000032000000, Flags 0x00000010, UUID 44324c55-8d39-e368-b65d-dac68e38d9fe, Type 0x97d7b011persist: Offset 0x000000004018c000, Length 0x0000000002000000, Flags 0x00000010, UUID cb64d7de-70c8-0a8e-a7db-3cdacdf1b69e, Type 0x6c95e238usbmsc: Offset 0x0000000044000000, Length 0x000000003e800000, Flags 0x00000000, UUID c2146c4f-d77a-c9a0-5837-f41dcbd5d68a, Type 0x1b81e7e6cache: Offset 0x0000000084000000, Length 0x0000000010000000, Flags 0x00000010, UUID 9709b46c-0313-18e5-04ca-65e6a53d6ea2, Type 0x5594c694recovery: Offset 0x0000000094000000, Length 0x0000000002000000, Flags 0x00000010, UUID d704a802-32ef-8ffd-4663-0efcea08a944, Type 0x9d72d4e4devinfo: Offset 0x0000000096000000, Length 0x0000000000100000, Flags 0x00000010, UUID c8f83c34-31bd-df17-ceb8-75729f2c3e07, Type 0x1b81e7e6keystore: Offset 0x0000000098000000, Length 0x0000000000080000, Flags 0x00000000, UUID 99b6c311-2a4c-63fc-66fa-e3a3c2b028d4, Type 0xde7d4029oem: Offset 0x0000000098080000, Length 0x0000000004000000, Flags 0x00000000, UUID a1f340a8-8e47-272a-d5d9-9da01a615bfb, Type 0x7db6ac55config: Offset 0x000000009c080000, Length 0x0000000000080000, Flags 0x00000000, UUID 668ac29d-5cb3-22d8-81d7-1c0f69ef6c1a, Type 0x91b72d4duserdata: Offset 0x000000009c100000, Length 0x000000004fefbe00, Flags 0x00000000, UUID 80d928b2-abc2-3586-5276-c31952ae4cb0, Type 0x1b81e7e6
You can also dump the raw partition table into a file with the comman -gpt [filename] option, like this:
python3 edl.py -loader generic_CAT_B35.mbn -gpt gpt.img
Partition readback
You can backup any partition from the device with -r [partname] [filename] option, for instance:
python3 edl.py -loader generic_CAT_B35.mbn -r recovery recovery.img
This will save the recovery partition contents into the recovery.img file.
Erase a partition
Supply the -e [partname] option, for example to erase "userdata":
python3 edl.py -loader generic_CAT_B35.mbn -e userdata
Flash a partition
Supply the -w [partname] [filename] option, for example to replace the userdata:
python3 edl.py -loader generic_CAT_B35.mbn -w userdata userdata.img
This will write the userdata partition contents from the userdata.img file. The edl.py utility also allows raw sector-to-sector writing but you're welcome to see the command help yourself if you need to do this.
Reboot the device
After you're done with all necessary operations, it's convenient to reboot the device into a normal mode with -reset option:
python3 edl.py -loader generic_CAT_B35.mbn -reset
DIY universal EDL cable
1. Get a spare microUSB cable and strip the insulation somewhere in the middle;
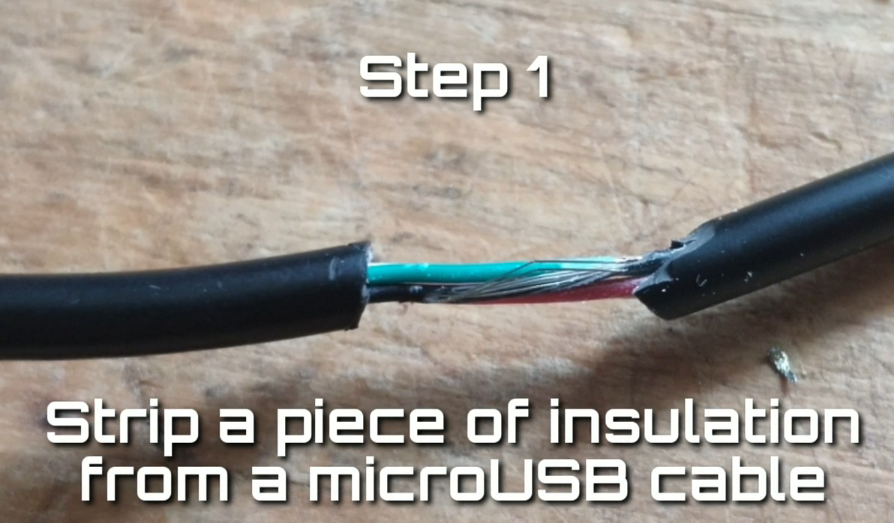
2. Detect the D+ and GND wires (usually green and black) and strip the insulation on them.

This operation is necessary to allow the two cables to connect temporarily to send the signal to the PC that a device in EDL mode is connected (see the following diagram).
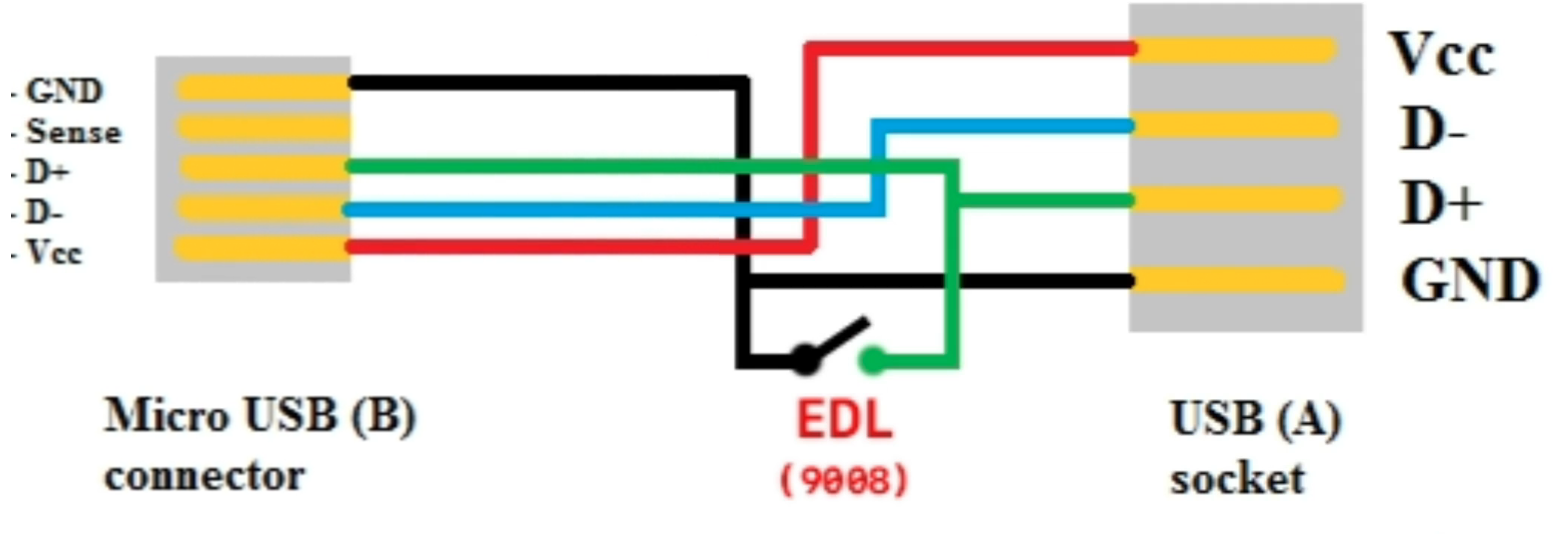
Turn off the phone and connect the microUSB end of the cable to it, press the stripped wires against each other and connect USB plug to the PC;
Keep holding the wires for at least 5 seconds, then disconnect them from each other;
After this, disconnect the wires from each other. Now the PC should detect the phone in EDL mode / USB PID 9008.
You have just transformed a simple, common and inexpensive microUSB cable into a necessary tool to perform operations in EDL mode on Qualcomm-based devices. In fact an official cable with connector and which may require welding would require costs and not easy availability.
Disassemble the phone (risky method)
This guide was provided by Victor C. on Google Groups, that wanted to share a quick write-up on accessing EDL where button combinations / USB cable don't work (since "access ELD mode" is not always simple), using its Canadian carrier-branded Alcatel A405DL. It's not exactly the same as US unlocked A405DL so none of other methods worked for EDL. And for him EDL was required to do "userdata" partition read / write with CAT B35 firehose like others have successfully done in the previous tests (see above).
For Victor, this method will work for most Qualcomm chipsets that support EDL, as long as manufacturer wired EDL pin somewhere on the board, sure that most of them have it since this undocumented feature helps should be needed to remove the back cover, find the ground, keep shortening different test-points to the ground until you find the one that triggers EDL mode. There is a slight risk of damaging the phone.
So, let go see the detailed steps!
Use testpoints to access EDL
Remove battery and rear cover of the phone exposing various test points. Connect phone to the computer with USB cable. Run a repetitive probe of usb devices list. In linux it can be infinte bash loop: "while true; do lsusb; sleep 1; done";
Find a ground point which is any large piece of metal e.g. sim card socket, sd card socket, RF shielding etc. Prepare two probes shorted to each other or a stiff thin wire. Multimeter with leads connected to a 10A socket of the multimeter is the best option as it's also allowing you to see when you short some wrong pins;
The phone will be rebooting on it's own while plugged into USB (if yours doesn't then you need to boot it by hand each time you try a new test-point). Go ahead and short different test-points to the ground one-by-one and observe boot behavior. Depending on which test point you short to the ground you can see:
a) Multimeter shows nothing, "lsusb" shows nothing, phone keeps rebooting - move to the next test-point
b) Multimeter shows nothing, "lsusb" shows nothing, phone does not boot - move to the next test point
c) Multi meter shows current of a few 100's mA, phone does not boot - remove your leads ASAP, as you a shorting a power line and risk damaging the phone. Move to the next test-point
d) Multimeter shows nothing, "lsusb" starts showing device ID "05c6:9008" - congratulations you are in EDL mode
....
z) something else happens and you phone no longer boots - sorry, for the next KaiOS phone you may want something that supports apps side-loading
Once you determine correct test-point for edl, you may want to drill a small hole in the back cover around the same place so you can keep it accessible with cover on the phone. Pictures illustrating EDL testpoints on A405DL:

no cover

modified cover
5. Once you know how to get into edl, use a matching firehose, edl.py to read / write "userdata" partition.





